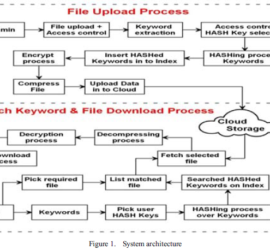
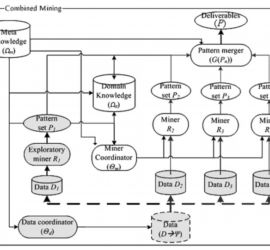
Data Mining Techniques in Cyber Crimes
Applying Data Mining Techniques in Cyber Crimes Abstract— Cyber-crime is crime that involves a computer and a network. The computer may have been used in the commission of a crime, or it may be the target.Globally the internet is been accessed by enormous people within their restricted domains. When the […]